Recently, the research work titled "Poisoning Attacks to Local Differential Privacy for Ranking Estimation" by the Data Security and Privacy Protection team at the School of Cyber Science and Technology was accepted by ACM CCS, a top-tier conference in network and system security. This work systematically exposes novel poisoning attack risks in ranking estimation tasks under Local Differential Privacy (LDP), proposes a multi-protocol attack framework with theoretical guarantees, and establishes a critical benchmark for the security defense of LDP systems. The first author of this work is Pei Zhan, a master's student at the school, with Associate Professor Peng Tang serving as the corresponding author.
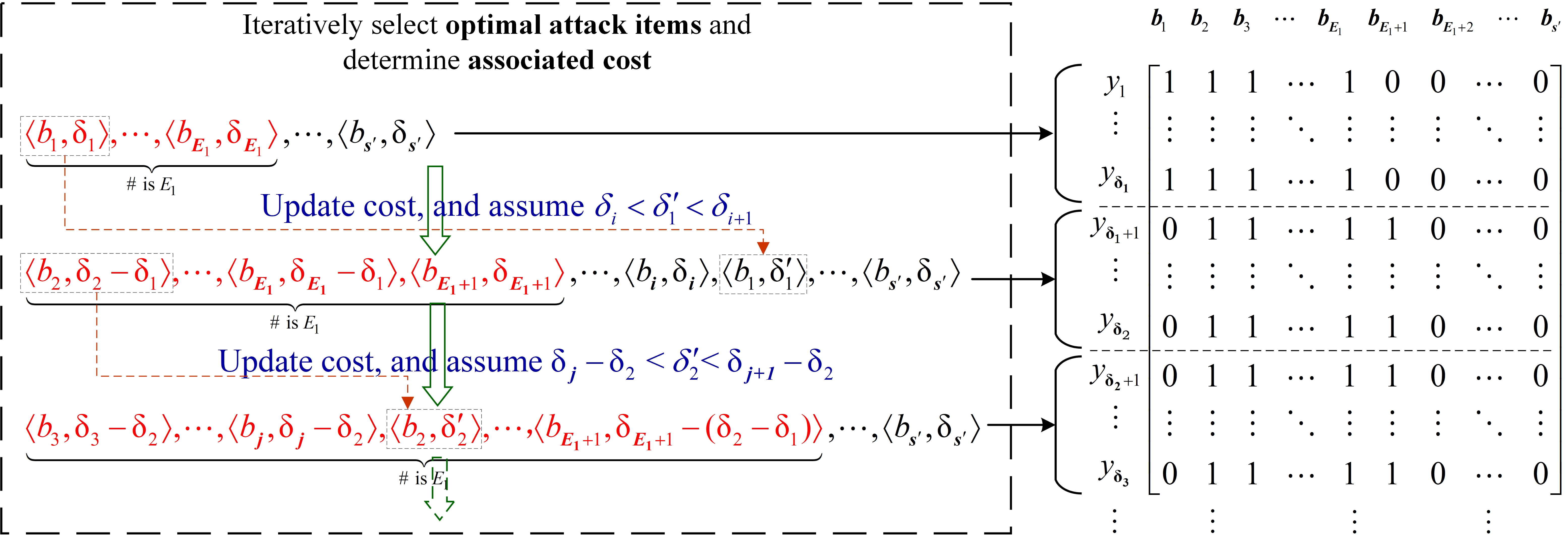
Local Differential Privacy (LDP), as a core technology in privacy computing, achieves privacy protection through client-side data perturbation and has been widely adopted by major internet platforms for data statistics. However, since LDP relies on users to perform perturbations autonomously, fake users can manipulate aggregated results by submitting carefully crafted poisoned data, leading to degraded data quality or misleading conclusions. To further investigate such attacks against LDP, this study proposes a precision frequency manipulation attack model for ranking estimation, enabling precise control over target item rankings with a limited number of fake users, significantly improving attack efficiency. The work introduces a quantitative theory for attack cost, defines optimal criteria for selecting attack items, and covers three mainstream LDP protocols—kRR, OUE, and OLH—achieving unified cross-protocol attack modeling.
For the kRR protocol, an iterative attack item selection algorithm is designed and proven to approximate the global optimal solution. For the OUE protocol, a frequency increment coupling strategy is proposed to address the challenge of joint optimization across multiple attack items. For the OLH protocol, a harmonic cost function based on hash preimages is introduced to achieve coordinated optimization between hash functions and attack items. Additionally, a confidence-level control module dynamically adjusts the number of attack iterations. This work aims to provide a standardized attack benchmark for LDP system security evaluation, promoting a paradigm shift in privacy computing from pure protection to protection-attack-defense collaborative research.
ACM CCS is a flagship security conference organized by ACM SIGSAC. Alongside IEEE S&P, USENIX Security, and NDSS, it is recognized as one of the four top-tier international academic conferences in network and system security worldwide and is listed as a CCF-A conference by the China Computer Federation (CCF). It represents the highest academic standard in the field, with research outcomes exerting significant influence on both academia and industry.
By Pei Zhan and Anqi Xiao